Compromise Detection Detail.
COMPROMISE DETECTION
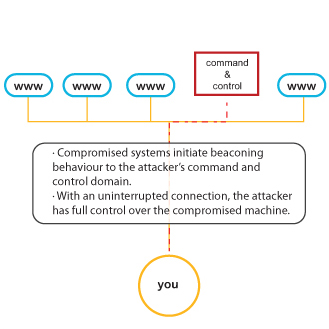
The first thing a system will do when compromised is call home. This command and control domain the system connects to gives instruction to the compromised machine, or bot. Once this is possible, the attacker has full control over the bot. He can exfiltrate company or customer data or personally identifiable information, or use the botted system to attack the internal network. In the case of DDoS attacks, (distributed denial of service), many compromised systems are used to disrupt service to an external network.
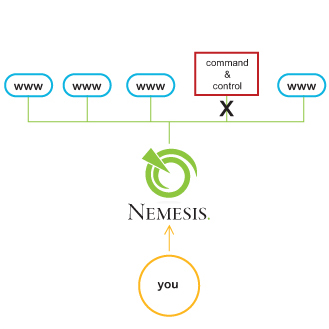
The malicious software can spread to other systems on your network, adding to the botnet membership. These machines are also then under the attacker's control. If a system becomes compromised, the Nemesis detection engine then automatically sets the mitigation tool in motion, adjusting its security rules in real time.
The compromise detection and mitigation engines work together,
keeping important data from leaving your network
by severing the connection to the attacker.
Nemesis can identify the back and forth communication between the botnet members and their command and control domain(s). This communication and the initial beaconing of new compromised systems looks different than normal network traffic and is classified as suspicious.
The suspicious domain(s) and the traffic signatures are correlated with Defence Intelligence's own database of known malicious domains, IPs, and signatures to formulate an identity for the new compromise. This feeds the mitigation system within Nemesis to stop the attack from continuing and the root cause of the initial compromise is determined to feed the prevention system of Nemesis, ensuring that similar future compromises cannot occur.
With every identified new compromise, the customer is notified with an alert. The Nemesis alerting system is one part of the management console accessible to the customer.
Find out more...
Nemesis Overview
Compromise Mitigation
Compromise Prevention